有機會兩個不同廠牌的設備實作IPSEC,不同廠牌就要注意IKE版本、加密、認證方式
以下是實作紀錄
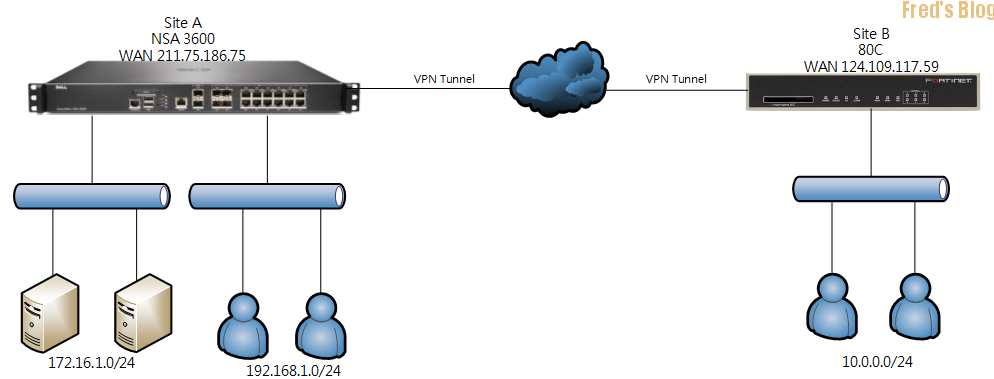
1. 環境架構圖
2. 設定IPSEC
1. 環境架構圖
|
Site A SonicWALL NSA 3600
|
Site B Fortigate 80C
|
||
|
Local Network
|
Remote Network
|
Local Network
|
Remote Network
|
|
192.168.1.0/24
172.16.1.0/24
|
10.0.0.0/24
|
10.0.0.0/24
|
192.168.1.0/24
172.16.1.0/24
|
|
Domain Name
|
Domain Name
|
||
|
abc.com
|
abc.com
|
||
2. 設定IPSEC
Note: IPSEC有一個很重要的前提,Local Network & Remote Network 不能重複
(如果真的重複就得靠NAT解決)
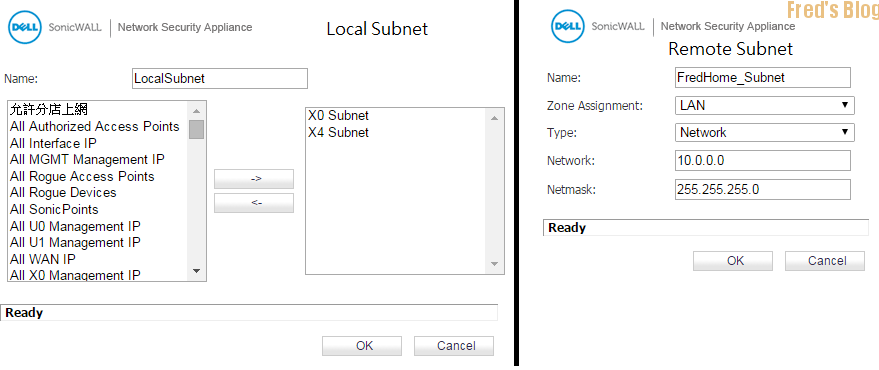
Site A SonicWALL 設定,建立Network Object
Network → Address Objects
A.設定IPSEC
VPN → Settings → Add
General 頁面
Name:To-80C
加入遠端防火牆WAN IP
Shared Secret: 兩台防火牆必須相同
NetWork 頁面
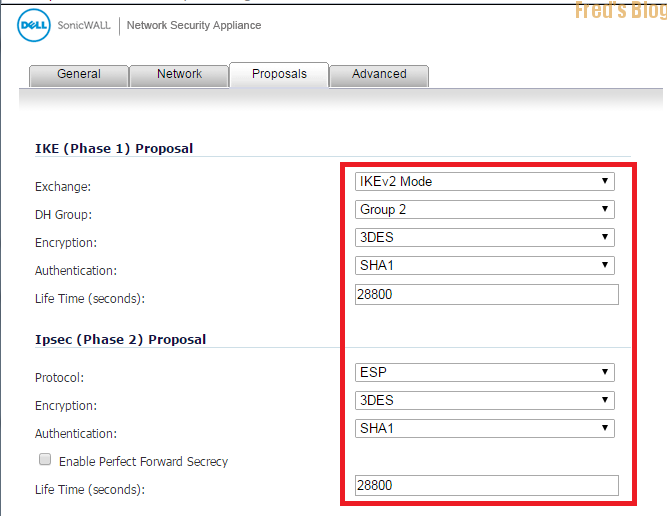
Proposals 頁面 (Fortigate 80C就是要比照辦理)
|
Phase1
|
|
|
Exchange
|
IKEv2
|
|
DH Group
|
2
|
|
Encryption
|
3DES
|
|
Authentication
|
SHA1
|
|
Life Time
|
28800
|
|
Phase2
|
|
|
Protocol
|
ESP
|
|
Encryption
|
3DES
|
|
Authentication
|
SHA1
|
|
Life Time
|
28800
|
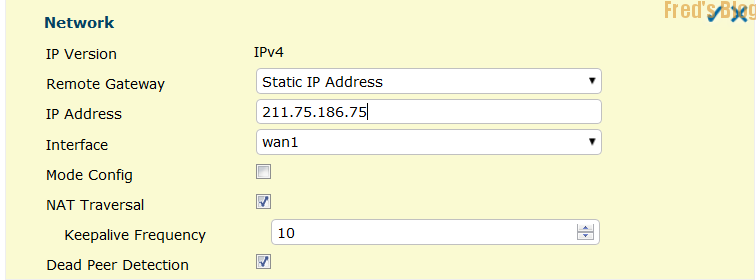
Site B Fortigate 設定
A.設定IPSEC
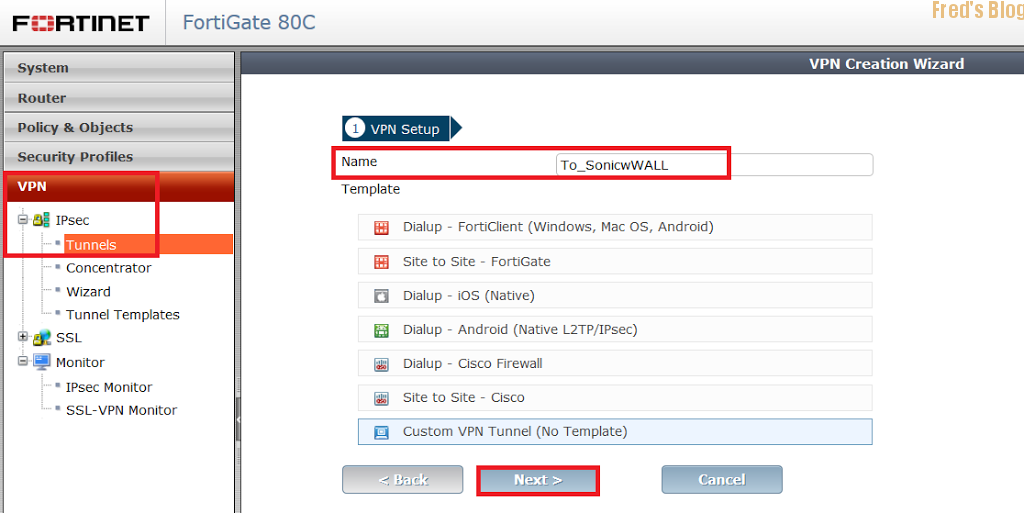
VPN → IPSec → Tunnels
Name To_SonicWALL
Custom VPN Tunnel (No Template)
加入遠端防火牆WAN IP
Interface 看從哪一個WAN去建立IPSEC
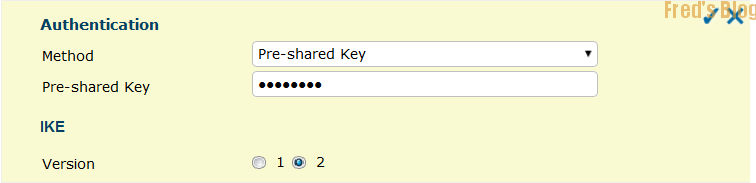
Shared Secret: 兩台防火牆必須相同
啟用IKE V2
Proposal Phase 1
|
DH Group
|
2
|
|
Encryption
|
3DES
|
|
Authentication
|
SHA1
|
|
Life Time
|
28800
|
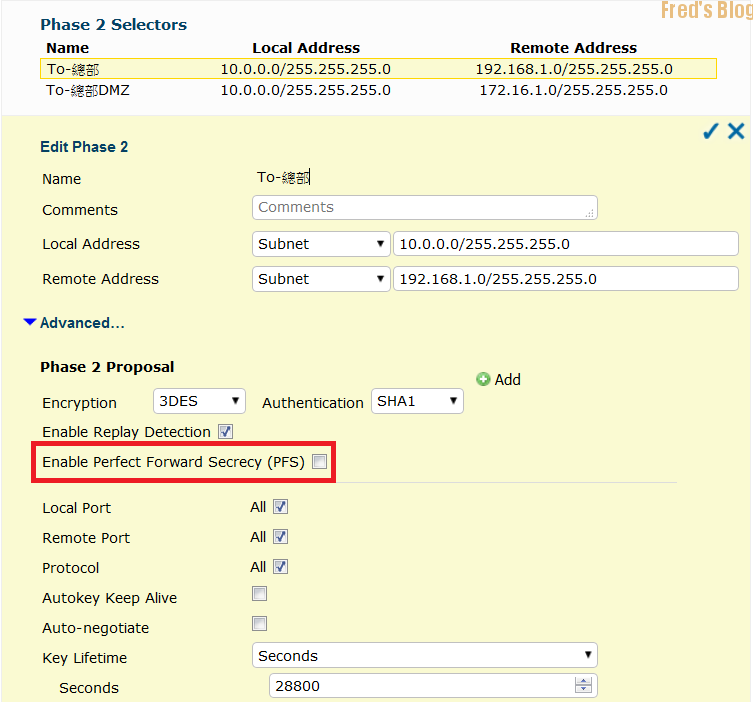
Proposal Phase 2
|
Encryption
|
3DES
|
|
Authentication
|
SHA1
|
|
Life Time
|
28800
|
不須選擇Perfect Forward Secrecy (PFS)
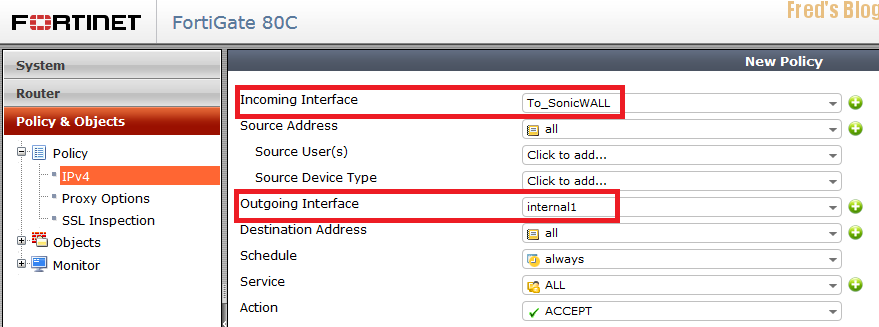
B.建立Policy
|
Incoming Interface
|
internal1
|
|
Outgoing Interface
|
To_SonicWALL
|
|
Incoming Interface
|
To_SonicWALL
|
|
Outgoing Interface
|
internal1
|
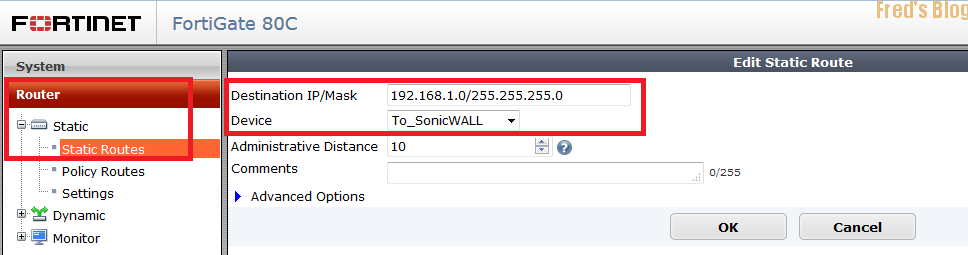
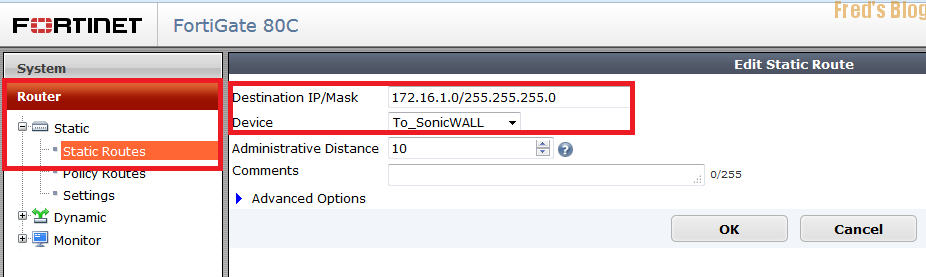
C.設定路由
192.168.1.0/24 >> To_SonicWALL
172.16.1.0/24 >> To_SonicWALL
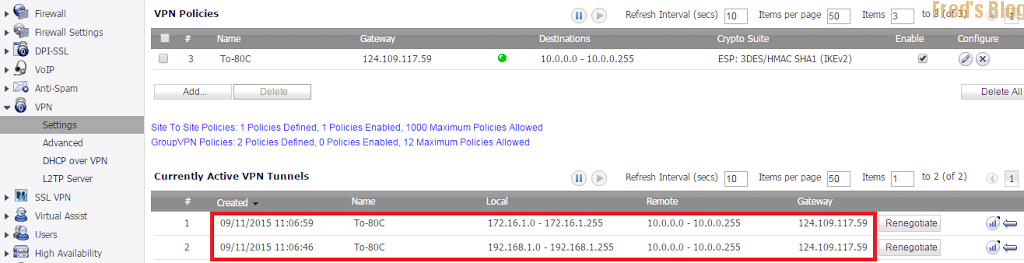
設定完成後確認VPN是否建立完成
Refer:
http://kb.fortinet.com/kb/viewContent.do?externalId=11657