針對Fortigate 我自己遇到的一些問題處理
1.HA問題
2.Switch Mode Interface Mode
3.LACP 設定
4.FortiClient無法安裝
5.LDAP帳戶無法登入
6.FSSO Polling-Mode debug
7.常用指令
8.參考文件
1.HA問題
啟用HA時,發生以下錯誤訊息
Please disable switch-controller first.
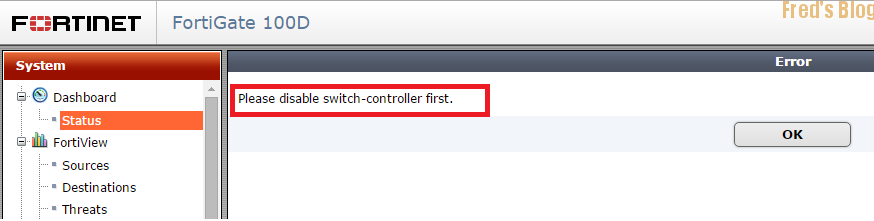
目前FortiOS 5.2 不支援Switch Controller HA (5.4後將支援) ,必須先關閉Switch Controller (此問題只有部分型號才會受影響),指令如下:
#config system global
(global) # set switch-controller disable
(global) # end
啟用HA時,發生以下錯誤訊息
get slave and master have different hdisk status. Cannot work with HA master. Shutdown the box!
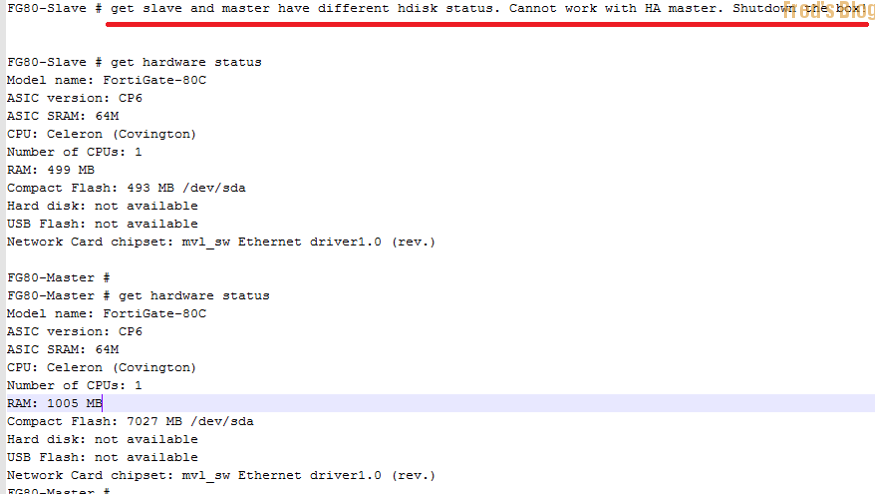
部分設備雖然型號一樣,但仍然無法建立HA Cluster,原因是設備底層的hardware reversion 不相同,必須使用以下指令來忽略 (忽略後需要重開設備)
以下機型可能會有這樣的問題產生,請注意
- FortiGate-100D
- FortiGate-300C
- FortiGate-80C and FortiWiFi-80C
- FortiGate-60C
#execute ha ignore-hardware-revision enable
2.Switch Mode Interface Mode
#config system global
(global)#set internal-switch-mode interface
(global)#end
Changing switch mode will reboot the system!
Do you want to continue? (y/n)y
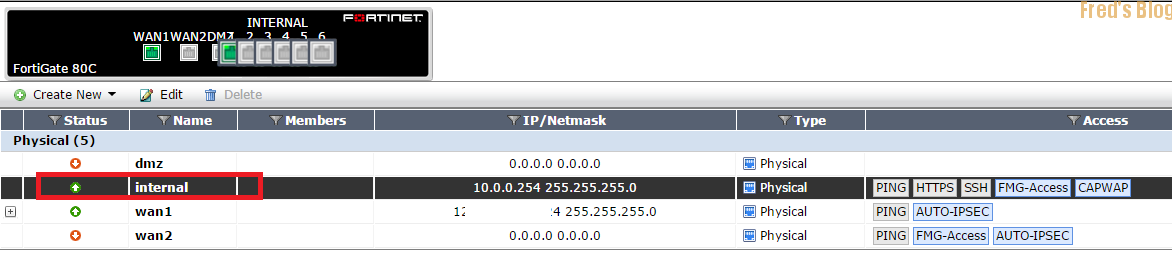
若跳出以下錯誤訊息,表示有物件使用到internal port,把它給刪除既可
Interface internal is in use attribute set operator error, -23, discard the setting Command fail. Return code -23
60D,70D,100D 預設都使用Hardware Switch
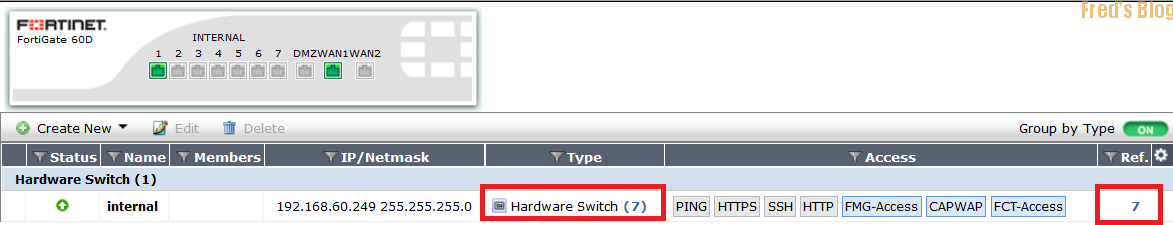
刪除方式如下 (一樣需要確認是否有物件佔用,否則也是無法刪除)
#config system virtual-switch
刪除Name
(virtual-switch) # delete ?
*name Name of the virtual switch. internal
(virtual-switch) # delete internal
3.LACP 設定
增加Port 1 & Port 2
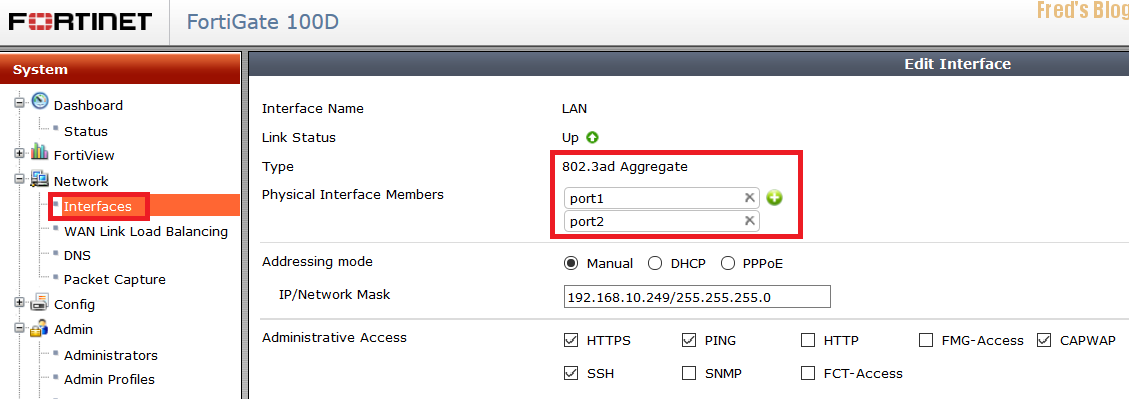
設定LACP mode Passive
#config system interface
(interface) #edit LAN
設定LACP mode dynamic passive
(LAN) # set lacp-mode ?
static use static aggregation, do not send and ignore any LACP messages passive passively use LACP to negotiate 802.3ad aggregation active actively use LACP to negotiate 802.3ad aggregation
(LAN) # set lacp-mode passive
(LAN) # end
4.FortiClient無法安裝
安裝時發生以下狀況
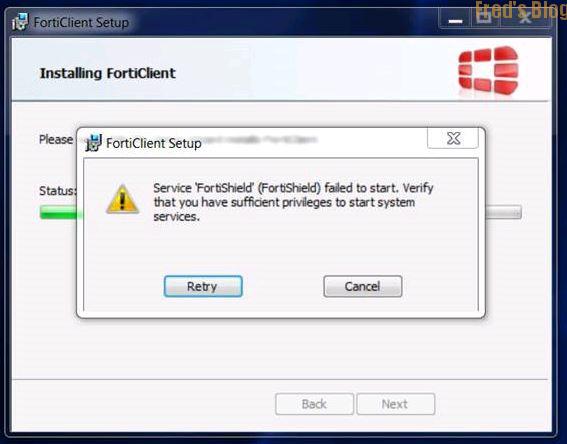
直接安裝以下安全性更新KB3033929
https://www.microsoft.com/zh-TW/download/details.aspx?id=46148
安全性更新說明
https://technet.microsoft.com/library/security/3033929
5.LDAP帳戶無法登入
測試LDAP連線正常,但是實際登入時卻又無法正常登入
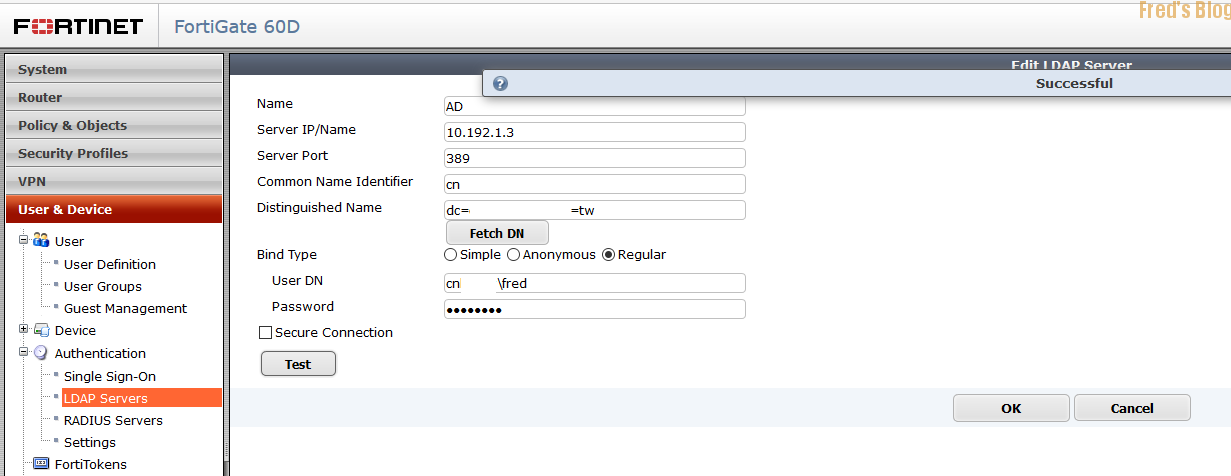
通常與Common Name Identifier參數有關,因為在建立AD使用者時, cn attribute並非是實際帳戶欄位,可嘗試使用sAMAccountName attribute可使用LDAP Browser確認
6.FSSO Polling-Mode debug
查詢SSO Polling mode 是否運作正常
#diag debug fsso-polling detail
AD Server Status: ID=1, name(10.192.1.3),ip=10.192.1.3,source(security),users(5) port=auto username=cnlinktw\administrator read log offset=123298750, latest logon timestamp: Fri Dec 16 10:31:28 2016 polling frequency: every 10 second(s) success(471), fail(0) 每10秒測一次 LDAP query: success(41), fail(7) LDAP max group query period(seconds): 0 Number of users logged in: Within 1 sec: 0(0.00%) Within 1-5 secs: 0(0.00%) Within 5-10 secs: 0(0.00%) Within 10-15 secs: 0(0.00%) Within 15-20 secs: 0(0.00%) Within 20-25 secs: 0(0.00%) Within 25-30 secs: 0(0.00%) Within 30-60 secs: 0(0.00%) Beyond 60 secs: 0(0.00%) most recent connection status: connected Group Filter: 塞選 Domain User CN=Domain Users,CN=Users,DC=cnlink,DC=net,DC=tw
查詢使用者登入哪台DC
#diag debug fsso-polling user 1
7.常用指令
查看Firmware 版本、SN
#get system status | grep Version
#get system status | grep Serial
查看目前誰登入了設備
#get system admin list
設定Fail2ban機制
#config system global
嘗試登入5次錯誤就封鎖
(global) # set admin-lockout-threshold 5
每次封鎖時間 300秒
(global) #set admin-lockout-duration 300
設定管理者登入數量10
(global) #set admin-login-max 10
查看目前連線狀況,配合grep擷取你想要的資訊
#get system session list | grep udp
查看路由表
#get router info routing-table all
重啟路由 (有時候路由不生效可以嘗試看看)
#execute router restart
查詢ARP,配合grep擷取你想要的資訊
#get system arp | grep 10.0.0.100
NAT IP 查詢,當有使用VIP或者IP Pool 要特別注意
查詢NAT VIP
#show firewall vip
查詢NAT ip pool
#show firewall ippool
設定開啟不對稱路由
#config system settings
(settings) # set asymroute enable
(settings) # end
關閉 Fortigate 使用SIP LAG
# config system settings
(settings) # set sip-helper disable
(settings) # set sip-nat-trace disable
需重新開機
設定SSLVPN 認證LDAP 若密碼到期可強制通過SSLVPN 修改密碼
# config user ldap
#set password-expiry-warning enable
#set password-renewal enable
設定SSH登入
#config system admin
(admin)#config system admin
(admin)#edit admin
(admin)#set ssh-public-key1 "ssh-rsa XXXXXXXX"
查看CPU、記憶體、Process 狀態
#diagnose sys top
Run Time: 330 days, 12 hours and 4 minutes 0U, 0N, 2S, 98I; 499T, 269F, 83KF miglogd 52 S 0.4 3.4 src-vis 76 S 0.0 7.9 pyfcgid 1904 S 0.0 4.3 pyfcgid 1906 S 0.0 4.3 pyfcgid 1907 S 0.0 4.3 pyfcgid 1908 S 0.0 4.3 httpsd 1087 S 0.0 4.2 httpsd 1089 S 0.0 4.2 cmdbsvr 34 S 0.0 3.9 httpsd 54 S 0.0 3.6 httpsd 1086 S 0.0 3.4 dnsproxy 84 S 0.0 3.3 ipshelper 63 S < 0.0 2.9 newcli 1923 R 0.0 2.7 newcli 1911 S 0.0 2.7 fgfmd 86 S 0.0 2.6 cw_acd 87 S 0.0 2.3 pimd 47 S 0.0 2.1 forticldd 65 S 0.0 2.0 fcnacd 67 S 0.0 1.9
| Letter | Description |
| U | User cpu usage (%) |
| S | System cpu usage (%) |
| I | Idle cpu usage (%) |
| T | Total memory |
| F | Free memory |
| KF | Kernel free memory |
| Column #1 | Column #2 | Column #3 | Column #4 | Column #5 |
| Process name | Process identification (PID) | One letter process status.
S: sleeping process R: running process <: high priority |
CPU usage (%) | Memory usage (%) |
Kill Process (類似Linux Kill)
SIGTERM (15):依照正常程序結束行程
SIGKILL (9):強制立即結束行程
SIGKILL (11):重新啟動行程
#diagnose sys kill 9 100
查看Fortigate 硬體狀態 (網卡狀態)
#get hardware nic wan1
查看Fortigate 硬體狀態 (CPU)
#get hardware cpu
查詢SSLVPN 詳細LOG
#diagnose debug application sslvpn -1
#diagnose debug enable
8.參考文件
Firmware 升級文件(Support Upgrade Guide)
http://cookbook.fortinet.com/sysadmins-notebook/supported-upgrade-paths-fortios
查詢Maximum Values Table (修改連結上的版本號,則可看到自己想要的版本號)
http://docs.fortinet.com/d/fortigate-fortios-5.2.7-maximum-values-table