常在網路上看到很多人說單一IP使用多個SSL網域,早期的確無法支援,但現在透過Server Name Indication (SNI) 已經實現單一IP使用多個SSL網域。
其實這一個功能需求大概只有Public IP比較少的人會使用到(中小企業環境),所以並非大部分人都會遇到的問題,這邊介紹針對Linux Apache & Barracuda Load Balancer ADC Server Name Indication (SNI) 介紹及設定
1. Server Name Indication (SNI) 介紹
2. CentOS Apache 設定SNI
3. Barracuda Load Balancer ADC設定SNI
1. Server Name Indication (SNI) 介紹
單一IP上有多個SSL網站,早期在做SSL交握時,此時Server 必須要把憑證傳送給Client,若Web Server 不知Client需要連哪一個SSL網站時,就無法傳送正確的憑證到Client上。
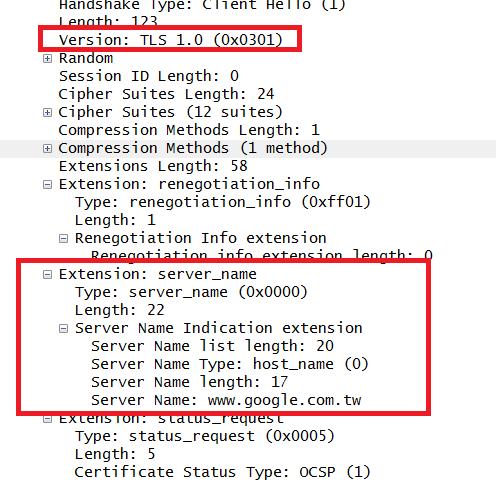
目前在做SSL交握時,Client會先發送TLS的延伸協議 Server Name Indication,來通知Web Server要連哪一個網站,此時Web Server會看到SNI,就可授予Client正確的憑證
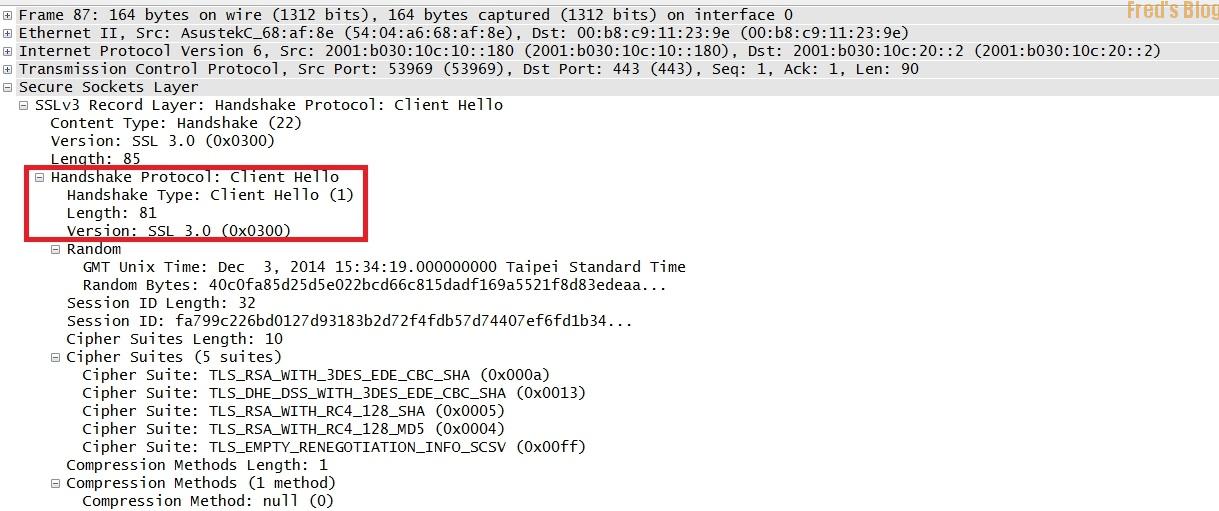
早期使用SSL Version 3,Client Hello尚未支援SNI時的封包,故單一IP無法使用多個SSL 網域
目前透過TLS 1.X以上,Client Hello 支援延伸SNI的封包,Web Server可以是單一IP使用多個SSL網域
Note: Windows XP + IE 8 就算使用TLS v1.0仍然不支援SNI
2. CentOS Apache 設定SNI
單一IP使用多個SSL網域
產生SSL憑證 & Key
#openssl req -new -keyout site1.key -nodes -x509 -days 3650 -out site1.crt
#openssl req -new -keyout site2.key -nodes -x509 -days 3650 -out site2.crt
移動Site1憑證& key到相關位置
#mv /root/site1.crt /etc/pki/tls/certs
#mv /root/site1.key /etc/pki/tls/private/
移動Site2憑證& key到相關位置
#mv /root/site2.crt /etc/pki/tls/certs
#mv /root/site2.key /etc/pki/tls/private/
WebSite1 VirtualHost設定
#vi /etc/httpd/conf.d/site1.conf
WebSite2 VirtualHost設定
#vi /etc/httpd/conf.d/site2.conf
重新啟動HTTP
#/etc/init.d/httpd restart
3. Barracuda Load Balancer ADC設定SNI
上傳憑證 & Key 到Barracuda Load Balancer ADC
Basic >> Certificates
Basic >> Service >> Add
|
SNI
|
Enable
|
開啟SNI功能
|
|
Strict SNI Check
|
Disable
|
當Client 瀏覽器不支援SNI時,則發送預設憑證
|
|
Strict SNI Check
|
Enable
|
當Client 瀏覽器不支援SNI時,則封鎖連線
|
+Add SNI Domain設定相對應網域 & 憑證
Refer:
http://wiki.apache.org/httpd/NameBasedSSLVHostsWithSNI
http://en.wikipedia.org/wiki/Server_Name_Indication
http://adc.barracuda.com/cgi-mod/view_help.cgi?password=15f261d80fb8ea5eb0a393879f7a8c02&et=1417599702&auth_type=Local&locale=en_US&user=guest&screen=services&transcreen=2601&title=Server%20Name%20Identification#Server Name Identification